Toughen your Cyber Defence
Despite the slew of fancy terminology littered throughout cybersecurity discussions, at its core, it’s underlying intentions are no different from that of your conventional burglar.
Aside from the obvious technical differences, the classification of threats faced by SMEs today is no different from those experienced by our folks back in the old days
Reputation damage, operational disruption or loss of proprietary information or other strategic assets are some common after effects of a cyber attack
Losing your crucial corporate or business information can lead to loss of customers and business. Cyber attacks can disrupt your business. With security as a service offering, your business is protected by us 24/7 with a dedicated support team. We protect your business while you focus on growing your business
93%
OF SMALL BUSINESSES HAVE BEEN COMPROMISED AT LEAST ONCE A YEAR
Why Cybersecurity is Important?
It’s not just big businesses who need to worry about cybersecurity. No business is too small to be at risk of a cybersecurity attack, it does happen to small to medium business too.
And as more businesses move towards cloud storage, the use of cryptocurrencies increases, coupled with a post GDPR world and this problem becomes ever more complicated.
A breach can happen even if the business’s own corporate network has the necessary level of protection — through supply chain attacks or breaches as a result of vulnerabilities in third-party legitimate software.
Does your business need to comply with data protection legislation? If so, you will be required by law to protect this information or risk being fined in the event of a security breach, further increasing the cost of an attack to your business.
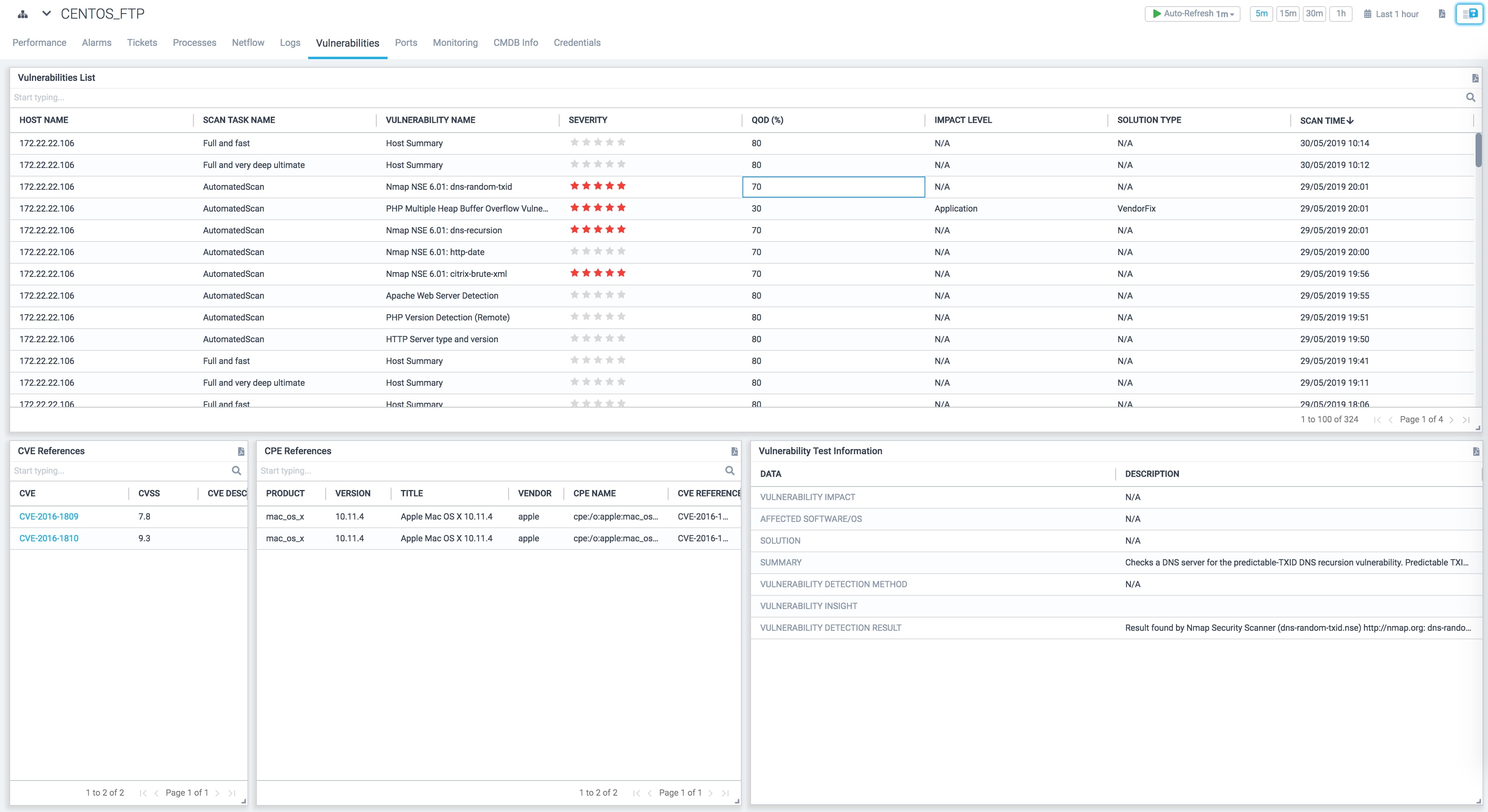
Vulnerability Management
Run automated Vulnerability Detection to identify any weaknesses in your assets and network. A simple unintentionally opened port can provide backdoor access to a malicious outsider who can exploit your data, information and assets.
Fix and patch vulnerabilities that exist in your network and track them over time. Stay up to date with the latest software versions and ios updates.
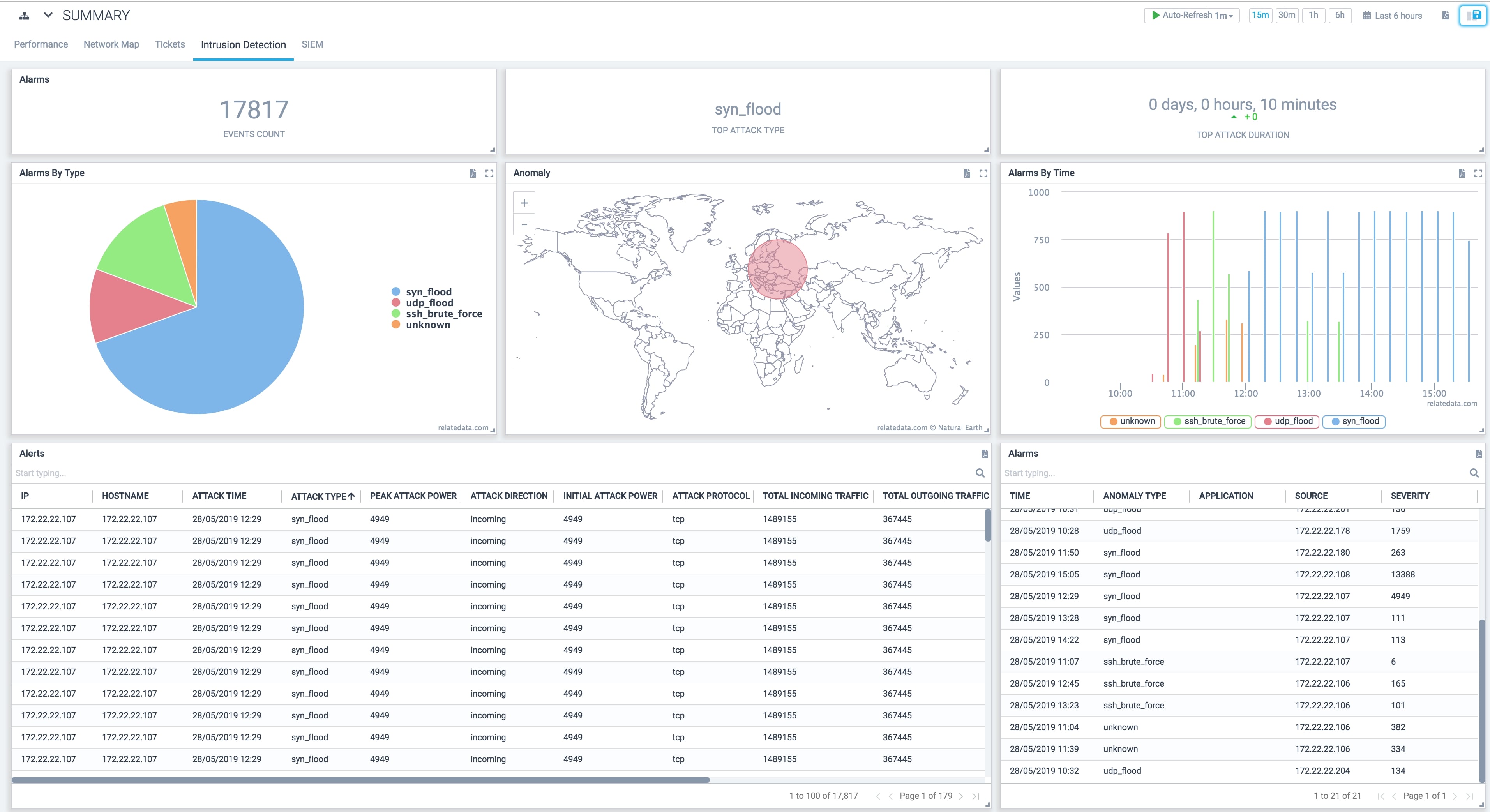
Intrusion Detection
Analyze and monitor network traffic for signs that indicate attackers are using a known cyberthreat to infiltrate or steal data from your network. Detect several kinds of behaviours like security policy violations, malware, and port scanners in real time.
Detect insider abuses or unauthorized file modifications. Maintain confidentiality, integrity and availability of your business and assets.
DDoS Protection
Keep your web services from being overwhelmed. Protect your website, API or web application from DNS flood attack that can make your business portal non-performant or completely unavailable.
Shield yourself against amplified traffic that can overwhelm a target network or server that is business critical.
Endpoint Security
A centralized approach to protecting all endpoints - servers, desktops, laptops, smartphones and other IoT devices - connected to the corporate IT network from cyber threats. Take corrective action without any manual intervention.
Anti-spyware, anti-spam, anti-malware and virus protection for your endpoints. Track USB port usage, software installations, policy violations, network and device usage analytics, port monitoring and user time tracking in real-time.
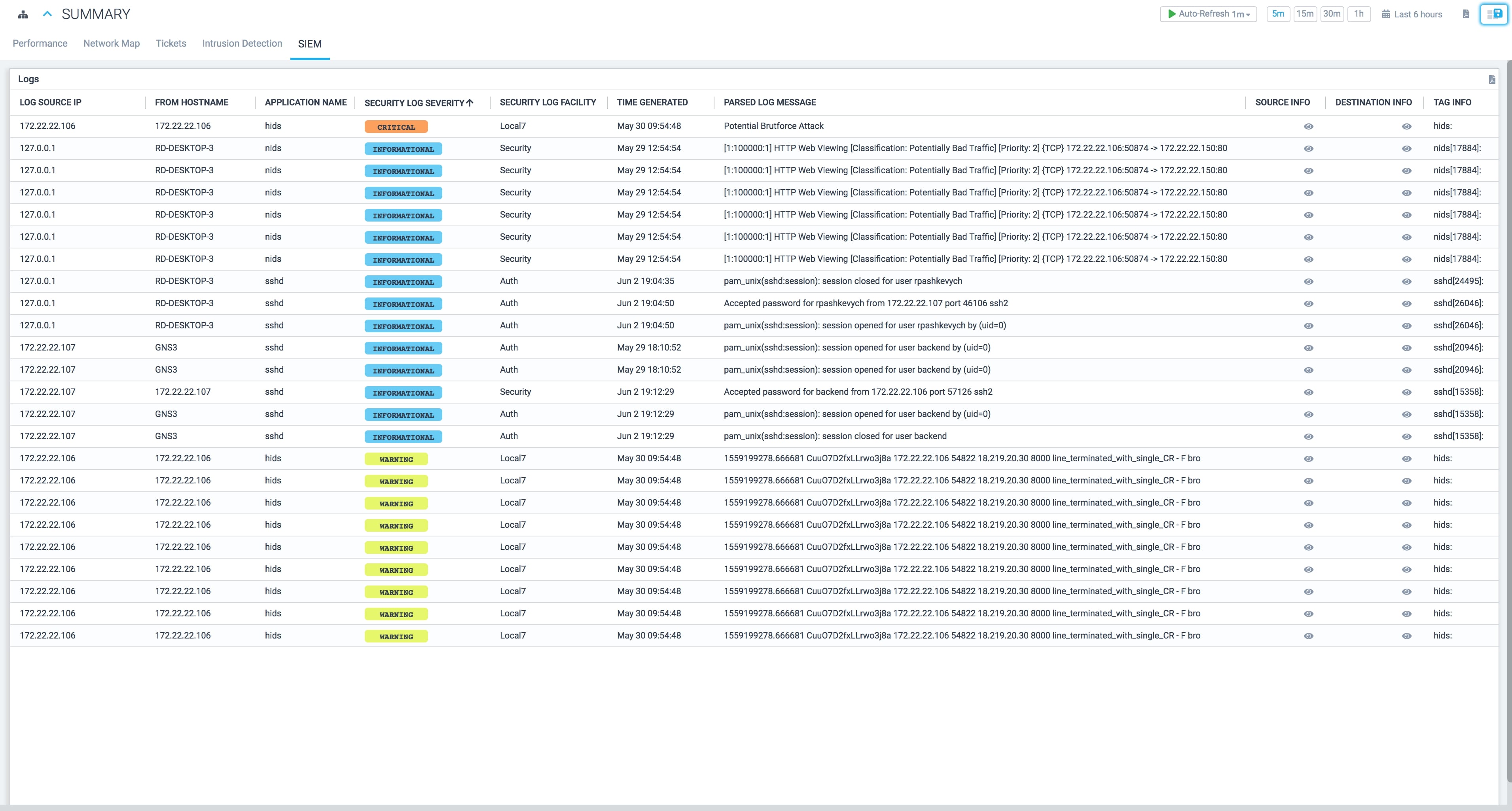
SIEM
Active patrol for your network to spot any signs of trouble. Shift from prevention to detection and remediation for detected threats. Leverage automated active response and notifications so you can focus on your business while we secure your assets, network and data.
Prevent Reputation damage, operational disruption or loss of proprietary information.
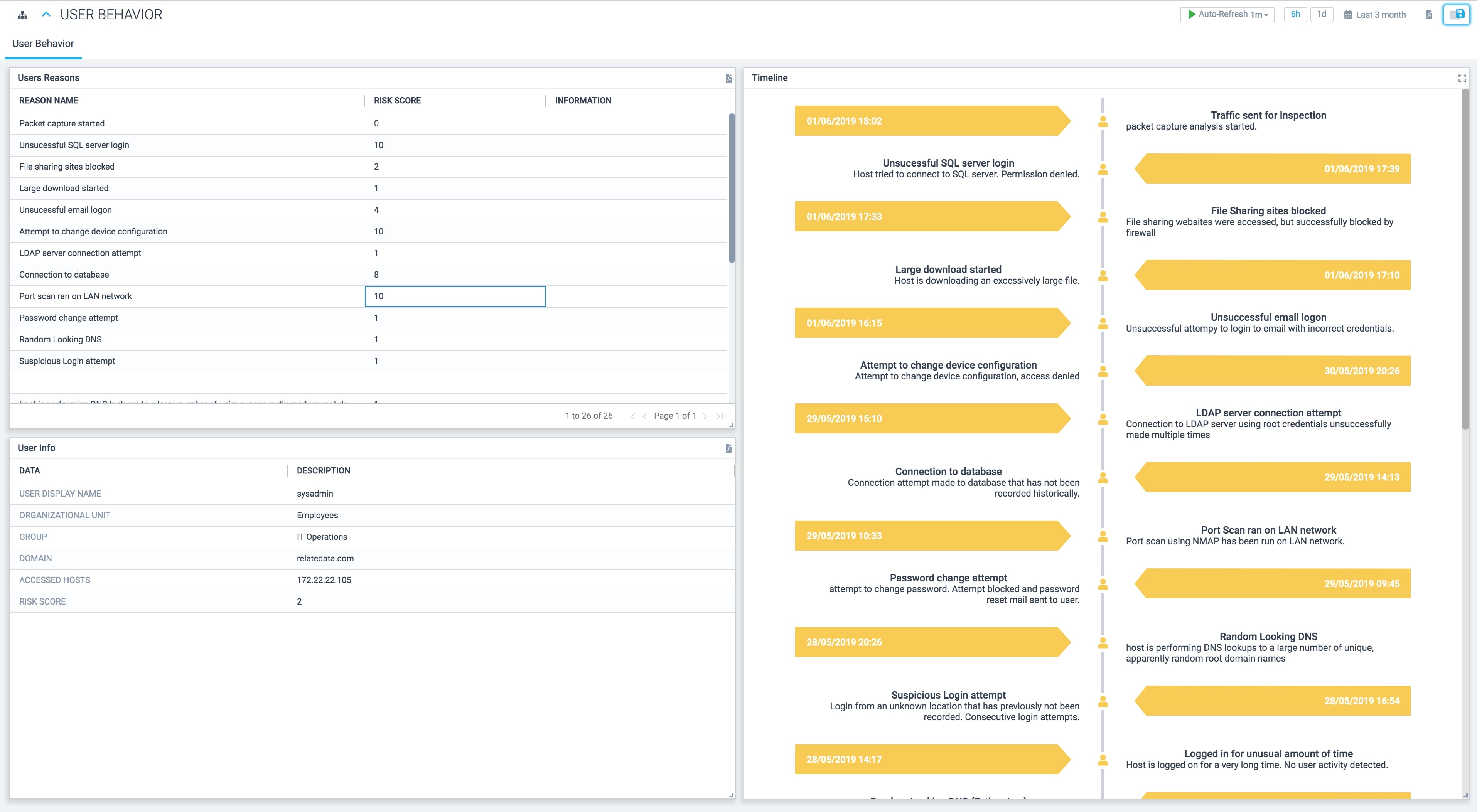
UEBA
Greater visibility and understanding of continuous user activity, detect threats and unusual behaviours by taking note of the normal conduct of users and assets.
Statistical analysis to show deviation and anomalies that could result in a potential real threat via established patterns leveraging machine learning.