Secure your business from cyber attacks and malicious intents in under 30 minutes
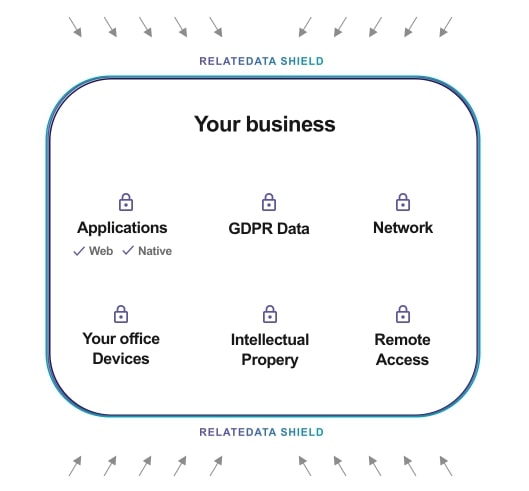
Your assets create value in your business. Protecting these assets from external and internal threats ensures peace of mind and continuous operation as an business.
Managing and securing your assets is always time-consuming and resource intensive. We protect your assets and provide “Security as a Service” where we continuously monitor your assets and monitor any unusual activity.
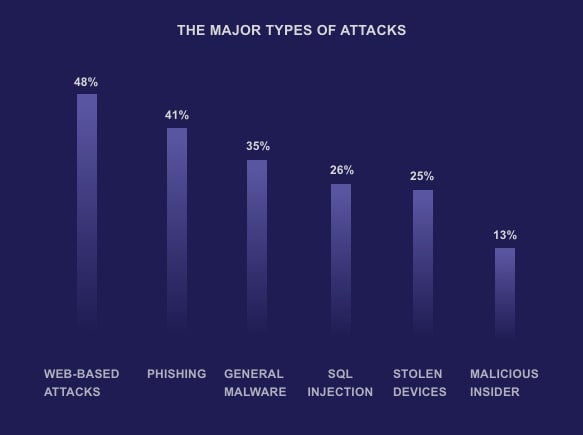
SECURE YOUR FUTURE NOW45% of cyber attacks target small business
Most of the companies go out of business within six months of a major cyber attack
Most of the companies go out of business within six months of a major cyber attack
As a business owner, your number one challenge is to grow the business. Your job is difficult, stressful and demanding and you may think that I take care of security later. Yes you can but it comes with a great risk: The future of your business
You may be surprised to know that the most cause of cyber attacks is due to an oversight of internal security policies and practices.

Optimise your network. Improve your application and network performance. Make sure your IT and business operations never halt
NETWORK PERFORMANCE
Monitor your hardware and software, optimise IT, reduce downtime for your business-critical applications and measure the quality of network services.
FAULT MANAGEMENT
Prevent, detect and correct faults in network, applications, hardware or software and optimise the network, storage and application performance.
UNIFIED LOG MANAGEMENT
Stay ahead of potential problems, speed up your troubleshooting processes and develop superior measures for dealing with unwanted issues and improve business operations.
APPLICATION MONITORING
Improve the performance, stability and user experience of your applications by identifying bottlenecks in real time and limit the impact on end users.
CONFIGURATION MANAGEMENT
Successfully develop, build, distribute, and track your software. Faster data recovery in case of data and configuration loss and faster technology adoption. Reduce backup administration and increase business process automation.
INCIDENT MANAGEMENT/ RESPONSE
Restore normal service operation as quickly as possible and minimize the adverse impact on business operations, ensuring that agreed levels of service quality are maintained.

Effective cybersecurity to shield your business from potential insider and outsider cyber threats and data breaches
VULNERABILITY MANAGEMENT
Identify threats and the risks they pose. Proactively mitigate and prevent the exploitation of IT vulnerabilities which exist in your small business. Evaluate Risks so that possible patches and solutions can be formulated.
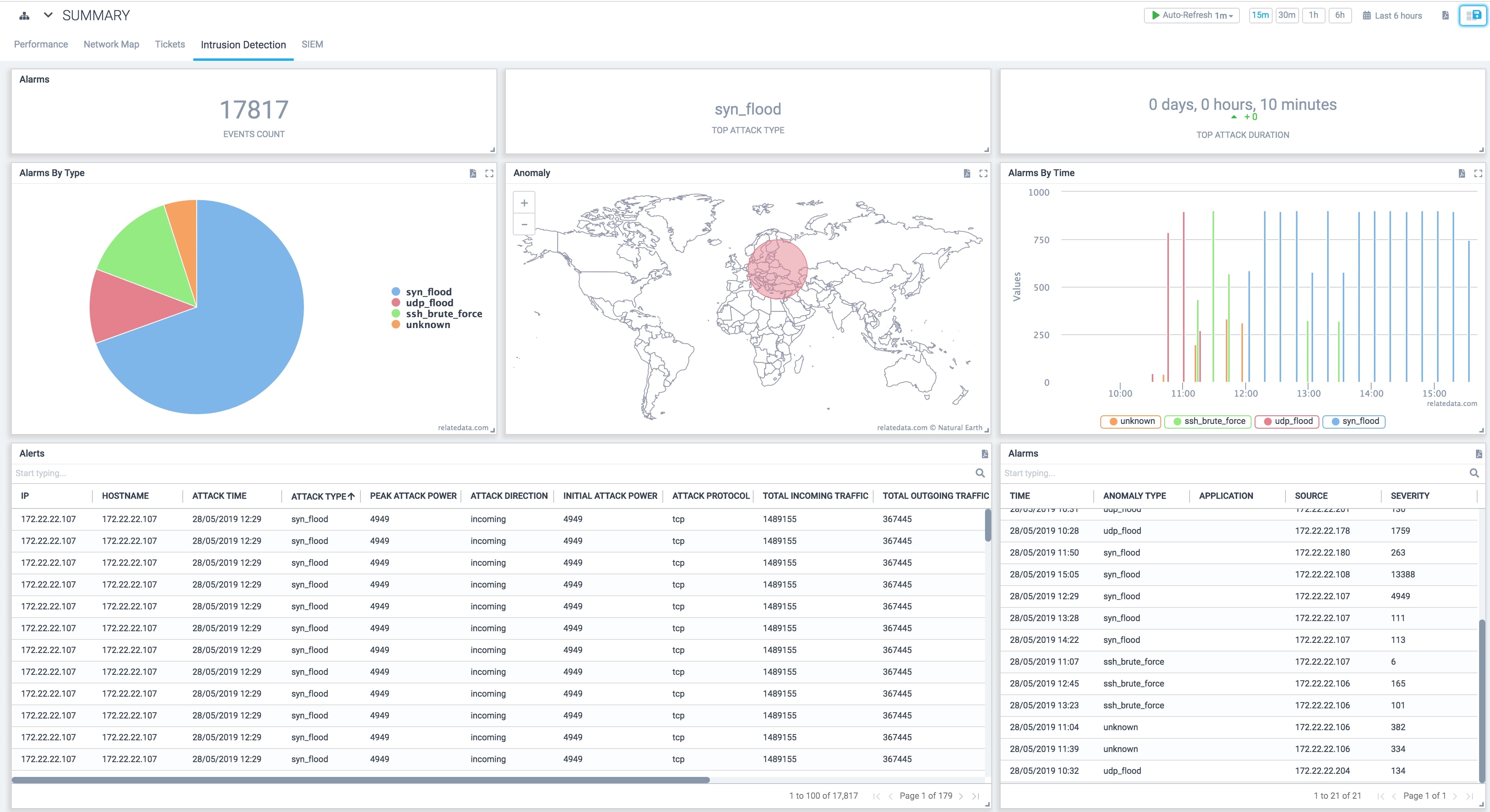
INTRUSION DETECTION
Constantly scan traffic flowing in and out of your corporate network for malware and suspicious activity. Detect in real time and stop them before they compromise your business and its assets.
DDOS PROTECTION
Prevent your site outage, protect your brand reputation, shield your revenue intake, and prevent data breaches.
ENDPOINT SECURITY
Track and continuously protect your assets. Monitor remote access and gateways into your network, shield your endpoints connected to the corporate network from vulnerable malicious threats.
SIEM (Security Information and Event Management)
Gather Threat intelligence though activities logged from various assets and applications, mitigate or totally thwart security threats that loom every day. Proactively manage and monitor phishing, malware and other malicious behaviours.
UEBA (User and Entity Behavior analysis)
Analyse behaviour across multiple users, IT devices and IP addresses, to detect complex attacks and stop insider threats.

Process and view actionable insights for high volume data from various sources to discover anomalies and attack patterns. Limit vulnerabilities of your assets and increase their resilience
Predictive Analytics
Proactively detect future incidents and maximize prevention. Help businesses identify security threats before they can do any damage.
Machine Learning
Data-centric algorithms and latest technologies to prevent threats in real-time and safeguard assets from any potential data breaches or intrusions.
Real-time Reporting
Non-stop Data collection & analysis to provide you with precise reporting for making snap decisions in heavily time-constrained situations.
Artificial Intelligence
Identify & analyze new exploits and weaknesses to mitigate further attacks. Effective decision making, quick resolution and consistent analysis.
Process Automation
Expedite the process of creating protections without straining resources, all while keeping pace with the attack.
Actionable Insights
Understand threats, threat actors and their capabilities. identify risks before they’re realised and mitigate attacks more effectively.